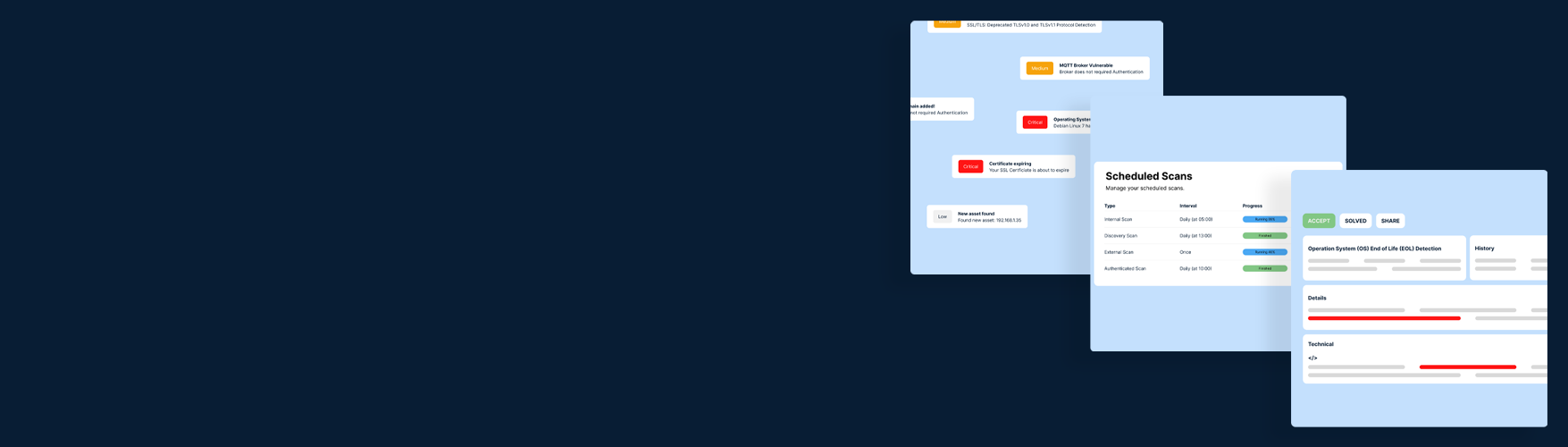
Enhance your customers' digital security by identifying, monitoring, and effectively resolving network vulnerabilities! With Vulnerability Management, vulnerabilities and Shadow-IT become a thing of the past. The solution makes it easy to discover weak points in the network and then provides advice on how to address them.
Be prepared for audits
With Vulnerability Management, every action related to vulnerabilities is easily recorded. The solution shows when a vulnerability was found and when it was resolved. The 'Audit trail' also helps with a subsequent audit or in the event of an incident. Vulnerability Management thus offers all the tools and functionalities to not only better secure the digital environment but also to be prepared for future audits and incidents. It does this by:
- Conducting internal scans on the internal network; from network devices to workstations and more.
- Conducting external scans, which reveal what a hacker can see from the outside. This makes vulnerabilities and points of attention visible.
- Conducting multi environment scans. Whether your customers work in the cloud, have a traditional network, or are hybrid - everything can be scanned for vulnerabilities.
- Performing scans and management according to organizational policies. Vulnerability Management helps your customer comply with these policies (ISO 27001, NEN 7510, BIO, and more).
- Conducting authenticated scans that bring to light vulnerabilities that may not be visible from the network. These devices can be scanned locally with the 'Authenticated Scan' to discover more weak spots.
- Exposing Shadow-IT. Vulnerability Management helps discover all hidden devices in the network - including information such as 'traceroutes', installed software, open network ports, and certificates.
- Marking vulnerabilities as accepted or resolved, including documentation to be prepared for future audits.
- Exporting data into a document that is readable for both executives and administrators. Export a report or use the SecurityHive API.